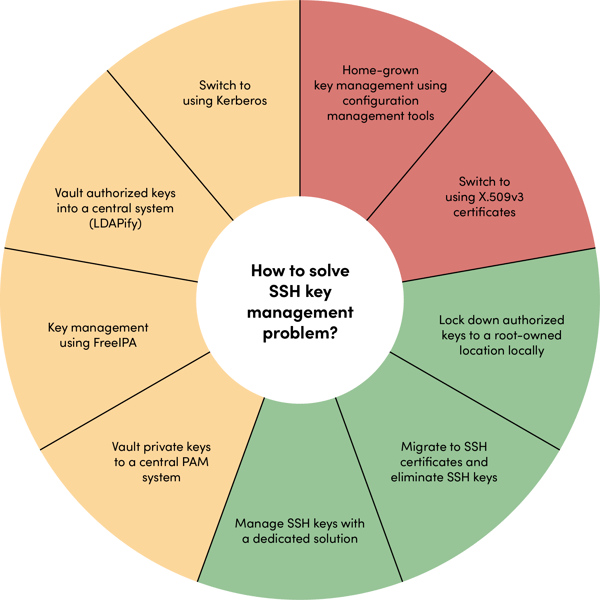
Learn about the most common ways of managing SSH keys
There are numerous ways to manage authentication keys. No matter which management method you prefer, choosing the wrong approach for your organization will eventually lead to:
- mismanagement of keys
- ineffective processes
- increased costs
- new vulnerabilities
- failed IT audits
To help you out, we put together this guide. It provides a comprehensive overview of the most common authentication key management approaches together with their strengths and weaknesses, rating them from the worst to the best ones.









.jpg?width=343&height=180&name=SSH_Centralized%20Password%20%26%20Key%20Management-02%20(1).jpg)


